When an HTTP request is received is a widely used trigger which is useful for integrating your flows with external systems or custom applications. With the new OAuth Authenitcation parameters this is more reliable as we can secure the flow using Microsoft entra ID authentication.
The Authentication Paramaters
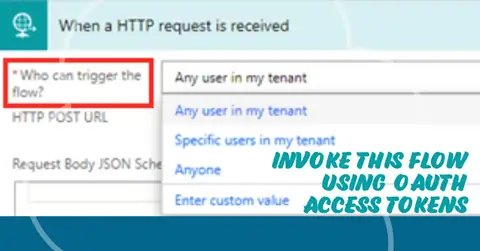
With the new capability to add OAuth authentication to this trigger, we have three paramaters which can be used
- Any user in my tenant
- Specific users in my tenant
- Anyone
While we are invoking this flow from any external application and if we are using the parameters 1 or 2 listed above, the external application should include the authentication headers to make a call to this flow.
Access Token Claims
An access token can be generated using OAuth which can then be added as a Bearer token in the request headers for calling the flow. The access token should have the following claims 1
- "aud": audience of the flow service.
- "iss": Issuer of the requestor
- "tid": tenant id of the requestor
- "oid": object id of the requestor. Optional. This field is required only if you have configured the trigger to restrict to specific users within the tenant.
Getting the access token
Register an Azure Entra ID App, and use the OAuth token endpoint to generate an access token, as shown below
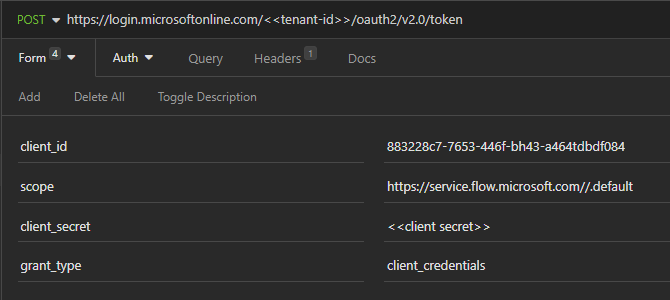
The scope in the above request is for "Public Cloud". For other cloud types refer the Audience Values.
Pay attention to the double slash (//) before .default in the scope URL. Without // you might receive an error with code - "MisMatchingOAuthClaims" and the message - "One or more claims either missing or does not match with the open authentication access control policy." The aud claim in the access token will have the correct value only if we specify // in the scope url
An access token is generated from the POST call. we can check the access token on https://jwt.ms to verify that it has all the required claims.
Sample response
{
"token_type": "Bearer",
"expires_in": 3599,
"ext_expires_in": 3599,
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSU......"
}
Invoking the Flow
A POST call can be made using this access token to invoke the flow
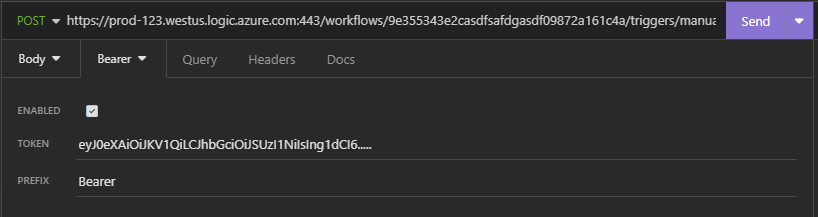
With this we should be able to invoke the flow which is secured using OAuth authentication. Making our automations more secure!
.